Starting an MFA Request Initiate secure Multi-Factor Authentication (MFA) requests seamlessly with HyperID's API
When it comes to starting Multi-Factor Authentication (MFA) requests for specific user actions, services should send a POST request to the HyperID API, requiring the 'mfa-client' scope, which should be granted during the user's authorization process.
Copy POST /mfa-client/transaction/start/v2 HTTP / 1.1
Host : api.hypersecureid.com
Content-Type : application/json
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6ImFjZDc0NGMzLWFlZDMtNGQxMC04ODZhLTcyYjU0MGY4NmU5YSJ9.eyJleHAiOjE2Nzk4MjM1NTEsImlhdCI6MTY3OTgxOTk1MSwiYXV0aF90aW1lIjoxNjc5ODE5OTUxLCJqdGkiOiIzM2ZlNzI2Ni1kOTY2LTRlNDgtYjU2My05ZWNhZTdjMWU3NTEiLCJpc3MiOiJodHRwczovL2xvZ2luLmh5cGVyc2VjdXJlaWQuY29tL2F1dGgvcmVhbG1zL0h5cGVySUQiLCJzdWIiOiI5MTZlMGUyZS00NmQ5LTRiODAtODg1Ni1kZDlmZWRiMWI3MjMiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJjbGllbnQtc2VydmljZS1hcHAiLCJzY29wZSI6Im9wZW5pZCBlbWFpbCBrZXlzIGF1dGgiLCJzaWQiOiI5OTVjNzhhZC1lYmFjLTRhYWYtOTdiZC0xOTQ4ZWMxOWQzNzEiLCJ3YWxsZXRfYWRkcmVzcyI6IjB44oCmIiwid2FsbGV0X2NoYWluX2lkIjoiMSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJlbWFpbCI6InVzZXJAZ21haWwuY29tIn0.h9GusuxDPX8VOjPoZHD73XzktOkVtd1qEz6C8AuBybw
Content-Length : 184
{
"template_id" : 1 ,
"values" : "" ,
"code" : "137" ,
"device_id" : "User device identifier" ,
"device_desc" : "User device description" ,
"ip" : "192.168.0.100"
} The authorization header should include a valid and non-expired bearer (access) token.
The template_id and values parameters are responsible for shaping the user interface and content of the MFA request within the HyperID Authenticator App. For more comprehensive information, please refer corresponding chapter: MFA Request Templates .
The code optional parameter will appear in the confirmation request within the HyperID Authenticator App. Users must ensure that the code in the app matches the one provided by the client service.
The device_id, device_desc, and ip are optional string parameters, used to provide users with information about the device that initiated the MFA request.
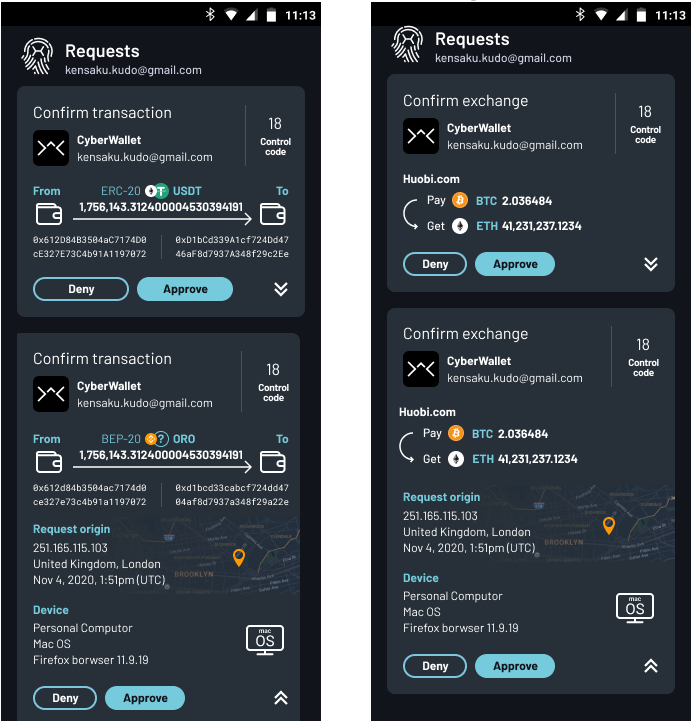
Below, you can see examples of how this information appears in MFA requests inside the HyperID Authenticator App. The top section displays the condensed UI version (the default view), while the section below showcases the expanded view (detailed information):
Upon a successful request, HyperID will respond with a JSON object containing the transaction_id, which can be used to Check the MFA request status or Cancel the MFA request :
Copy HTTP/1.1 200 OK
Content-Type : application/json
{
"result" : 0 ,
"transaction_id" : 1004
} The result field is an integer representation of request result, with various possible values as listed in the table below:
Result Value Meaning Failure because the service is temporarily unavailable
Failure due to invalid request parameters
Failure due to access denial
Failure due to an expired token
Failure due to an invalid token
Failure due to specified template is not found
Here are examples of the 'Start MFA request' implemented:
cURL JavaScript NodeJS Python C#
Copy curl -- location 'http://api.hypersecureid.com/mfa-client/transaction/start/v2' \
-- header 'Content-Type: application/json' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6ImFjZDc0NGMzLWFlZDMtNGQxMC04ODZhLTcyYjU0MGY4NmU5YSJ9.eyJleHAiOjE2Nzk4MjM1NTEsImlhdCI6MTY3OTgxOTk1MSwiYXV0aF90aW1lIjoxNjc5ODE5OTUxLCJqdGkiOiIzM2ZlNzI2Ni1kOTY2LTRlNDgtYjU2My05ZWNhZTdjMWU3NTEiLCJpc3MiOiJodHRwczovL2xvZ2luLmh5cGVyc2VjdXJlaWQuY29tL2F1dGgvcmVhbG1zL0h5cGVySUQiLCJzdWIiOiI5MTZlMGUyZS00NmQ5LTRiODAtODg1Ni1kZDlmZWRiMWI3MjMiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJjbGllbnQtc2VydmljZS1hcHAiLCJzY29wZSI6Im9wZW5pZCBlbWFpbCBrZXlzIGF1dGgiLCJzaWQiOiI5OTVjNzhhZC1lYmFjLTRhYWYtOTdiZC0xOTQ4ZWMxOWQzNzEiLCJ3YWxsZXRfYWRkcmVzcyI6IjB44oCmIiwid2FsbGV0X2NoYWluX2lkIjoiMSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJlbWFpbCI6InVzZXJAZ21haWwuY29tIn0.h9GusuxDPX8VOjPoZHD73XzktOkVtd1qEz6C8AuBybw' \
-- data '{
"template_id": 1,
"values": "",
"code": "137",
"device_id": "User device identifier",
"device_desc": "User device description",
"ip": "192.168.0.100"
}'
Copy var myHeaders = new Headers ();
myHeaders .append ( "Content-Type" , "application/json" );
myHeaders.append("Authorization", "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6ImFjZDc0NGMzLWFlZDMtNGQxMC04ODZhLTcyYjU0MGY4NmU5YSJ9.eyJleHAiOjE2Nzk4MjM1NTEsImlhdCI6MTY3OTgxOTk1MSwiYXV0aF90aW1lIjoxNjc5ODE5OTUxLCJqdGkiOiIzM2ZlNzI2Ni1kOTY2LTRlNDgtYjU2My05ZWNhZTdjMWU3NTEiLCJpc3MiOiJodHRwczovL2xvZ2luLmh5cGVyc2VjdXJlaWQuY29tL2F1dGgvcmVhbG1zL0h5cGVySUQiLCJzdWIiOiI5MTZlMGUyZS00NmQ5LTRiODAtODg1Ni1kZDlmZWRiMWI3MjMiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJjbGllbnQtc2VydmljZS1hcHAiLCJzY29wZSI6Im9wZW5pZCBlbWFpbCBrZXlzIGF1dGgiLCJzaWQiOiI5OTVjNzhhZC1lYmFjLTRhYWYtOTdiZC0xOTQ4ZWMxOWQzNzEiLCJ3YWxsZXRfYWRkcmVzcyI6IjB44oCmIiwid2FsbGV0X2NoYWluX2lkIjoiMSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJlbWFpbCI6InVzZXJAZ21haWwuY29tIn0.h9GusuxDPX8VOjPoZHD73XzktOkVtd1qEz6C8AuBybw");
var raw = JSON .stringify ({
"template_id" : 1 ,
"values" : "" ,
"code" : "137" ,
"device_id" : "User device identifier" ,
"device_desc" : "User device description" ,
"ip" : "192.168.0.100"
});
var requestOptions = {
method : 'POST' ,
headers : myHeaders ,
body : raw ,
redirect : 'follow'
};
fetch ( "http://api.hypersecureid.com/mfa-client/transaction/start/v2" , requestOptions)
.then (response => response .text ())
.then (result => console .log (result))
.catch (error => console .log ( 'error' , error));
Copy const axios = require ( 'axios' );
let data = JSON .stringify ({
"template_id" : 1 ,
"values" : "" ,
"code" : "137" ,
"device_id" : "User device identifier" ,
"device_desc" : "User device description" ,
"ip" : "192.168.0.100"
});
let config = {
method : 'post' ,
maxBodyLength : Infinity ,
url : 'http://api.hypersecureid.com/mfa-client/transaction/start/v2' ,
headers : {
'Content-Type' : 'application/json' ,
'Authorization': 'Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6ImFjZDc0NGMzLWFlZDMtNGQxMC04ODZhLTcyYjU0MGY4NmU5YSJ9.eyJleHAiOjE2Nzk4MjM1NTEsImlhdCI6MTY3OTgxOTk1MSwiYXV0aF90aW1lIjoxNjc5ODE5OTUxLCJqdGkiOiIzM2ZlNzI2Ni1kOTY2LTRlNDgtYjU2My05ZWNhZTdjMWU3NTEiLCJpc3MiOiJodHRwczovL2xvZ2luLmh5cGVyc2VjdXJlaWQuY29tL2F1dGgvcmVhbG1zL0h5cGVySUQiLCJzdWIiOiI5MTZlMGUyZS00NmQ5LTRiODAtODg1Ni1kZDlmZWRiMWI3MjMiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJjbGllbnQtc2VydmljZS1hcHAiLCJzY29wZSI6Im9wZW5pZCBlbWFpbCBrZXlzIGF1dGgiLCJzaWQiOiI5OTVjNzhhZC1lYmFjLTRhYWYtOTdiZC0xOTQ4ZWMxOWQzNzEiLCJ3YWxsZXRfYWRkcmVzcyI6IjB44oCmIiwid2FsbGV0X2NoYWluX2lkIjoiMSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJlbWFpbCI6InVzZXJAZ21haWwuY29tIn0.h9GusuxDPX8VOjPoZHD73XzktOkVtd1qEz6C8AuBybw'
} ,
data : data
};
axios .request (config)
.then ((response) => {
console .log ( JSON .stringify ( response .data));
})
.catch ((error) => {
console .log (error);
});
Copy import http . client
import json
conn = http . client . HTTPSConnection ( "api.hypersecureid.com" )
payload = json . dumps ({
"template_id" : 1 ,
"values" : "" ,
"code" : "137" ,
"device_id" : "User device identifier" ,
"device_desc" : "User device description" ,
"ip" : "192.168.0.100"
})
headers = {
'Content-Type' : 'application/json' ,
'Authorization': 'Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6ImFjZDc0NGMzLWFlZDMtNGQxMC04ODZhLTcyYjU0MGY4NmU5YSJ9.eyJleHAiOjE2Nzk4MjM1NTEsImlhdCI6MTY3OTgxOTk1MSwiYXV0aF90aW1lIjoxNjc5ODE5OTUxLCJqdGkiOiIzM2ZlNzI2Ni1kOTY2LTRlNDgtYjU2My05ZWNhZTdjMWU3NTEiLCJpc3MiOiJodHRwczovL2xvZ2luLmh5cGVyc2VjdXJlaWQuY29tL2F1dGgvcmVhbG1zL0h5cGVySUQiLCJzdWIiOiI5MTZlMGUyZS00NmQ5LTRiODAtODg1Ni1kZDlmZWRiMWI3MjMiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJjbGllbnQtc2VydmljZS1hcHAiLCJzY29wZSI6Im9wZW5pZCBlbWFpbCBrZXlzIGF1dGgiLCJzaWQiOiI5OTVjNzhhZC1lYmFjLTRhYWYtOTdiZC0xOTQ4ZWMxOWQzNzEiLCJ3YWxsZXRfYWRkcmVzcyI6IjB44oCmIiwid2FsbGV0X2NoYWluX2lkIjoiMSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJlbWFpbCI6InVzZXJAZ21haWwuY29tIn0.h9GusuxDPX8VOjPoZHD73XzktOkVtd1qEz6C8AuBybw'
}
conn . request ( "POST" , "/mfa-client/transaction/start/v2" , payload, headers)
res = conn . getresponse ()
data = res . read ()
print (data. decode ( "utf-8" ))
Copy var client = new HttpClient ();
var request = new HttpRequestMessage ( HttpMethod . Post , "http://api.hypersecureid.com/mfa-client/transaction/start/v2" );
request.Headers.Add("Authorization", "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6ImFjZDc0NGMzLWFlZDMtNGQxMC04ODZhLTcyYjU0MGY4NmU5YSJ9.eyJleHAiOjE2Nzk4MjM1NTEsImlhdCI6MTY3OTgxOTk1MSwiYXV0aF90aW1lIjoxNjc5ODE5OTUxLCJqdGkiOiIzM2ZlNzI2Ni1kOTY2LTRlNDgtYjU2My05ZWNhZTdjMWU3NTEiLCJpc3MiOiJodHRwczovL2xvZ2luLmh5cGVyc2VjdXJlaWQuY29tL2F1dGgvcmVhbG1zL0h5cGVySUQiLCJzdWIiOiI5MTZlMGUyZS00NmQ5LTRiODAtODg1Ni1kZDlmZWRiMWI3MjMiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJjbGllbnQtc2VydmljZS1hcHAiLCJzY29wZSI6Im9wZW5pZCBlbWFpbCBrZXlzIGF1dGgiLCJzaWQiOiI5OTVjNzhhZC1lYmFjLTRhYWYtOTdiZC0xOTQ4ZWMxOWQzNzEiLCJ3YWxsZXRfYWRkcmVzcyI6IjB44oCmIiwid2FsbGV0X2NoYWluX2lkIjoiMSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJlbWFpbCI6InVzZXJAZ21haWwuY29tIn0.h9GusuxDPX8VOjPoZHD73XzktOkVtd1qEz6C8AuBybw");
var content = new StringContent("{\r\n \"template_id\": 1,\r\n \"values\": \"\",\r\n \"code\": \"137\",\r\n \"device_id\": \"User device identifier\",\r\n \"device_desc\": \"User device description\",\r\n \"ip\": \"192.168.0.100\"\r\n}", null, "application/json");
request . Content = content;
var response = await client . SendAsync (request);
response . EnsureSuccessStatusCode ();
Console . WriteLine ( await response . Content . ReadAsStringAsync ());
Last updated 6 months ago